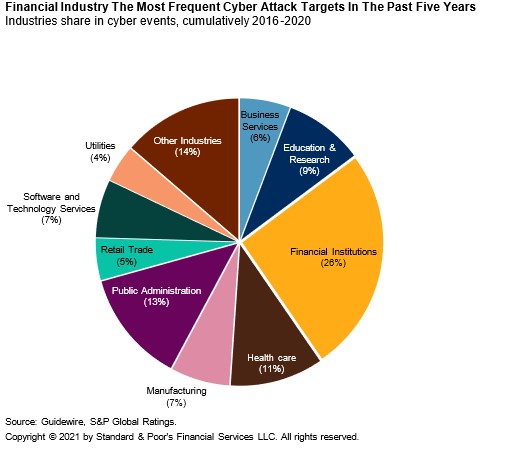
Cyber risk, the probability of loss and/or harm to an entity based on technological exposures, is much higher in the financial industry as compared to others, to the extent that even bank ratings can be greatly impacted. This certainly isn’t surprising given the nature of the data this sector manages every day.
While we always hear about the big cyberattacks, such as Accenture, CNA Financial, CapitalOne, Colonial Pipeline, SolarWinds, and Equifax, we don’t hear about the smaller financial organizations that are impacted daily by ransomware, business email compromises, unauthorized access, etc. Some of these attacks, which place sensitive data into the hands of online criminal enterprises, leave these small businesses in shambles due to the loss of productivity, brand damage, and soaring costs related to a cyber incident. Keep in mind that data obtained during a cyber incident can also be reused in later attacks, perpetuating a vicious lifecycle of damage to the digital assets of organizations and consumers alike.
This is why financial organizations of all sizes must adequately address their information technology and cybersecurity policies and controls to mitigate these risks in an effort to maintain consumer and investor trust. Once you know your risks, you can pinpoint specific actions to take to decrease the likelihood of an unwanted event or outcome.
Cyber Liability Insurance Market Updates and Considerations for Financial Institutions
As ransomware demands and associated insurance claims rise, the cyber insurance industry is combining their expertise by joining an alliance known as CyberAcuView, which brings together some of the biggest cyber insurance underwriters to help risk mitigation efforts by compiling and analyzing data related to cyber incidents and claims. This is a much-needed initiative to better understand how to protect against losses and manage cyber-related claims. Many cyber insurance carriers now require policyholders to implement continuous threat scanners, enable multi-factor authentication, and block all external access via remote desktop protocol (RDP). Failure to comply with these requirements can result in non-payment of claims or the inability to renew the insurance policy. Financial institutions should review their insurance policies to understand their policy limits, deductibles, and responsibilities to ensure they are covered in the event of a cyber incident.
Not all cyber incidents end in ransomware, but they can still be costly, which is why understanding your coverage is key. An analysis conducted by NetDiligence, an organization specializing in cyber risk readiness and responsive services, identified that ransomware was the number one cause of loss for SMEs ($90M average revenue). The study suggests that the average ransom demand jumped from $36K to $175K, while the average cost of a ransomware incident as a whole went from $150K to $275K. Additionally, the average incident cost for large companies ($8B average revenue) was $9.1M across all types of incidents. (These findings are based on 3,547 claims arising from events that occurred during 2015–2019.) These numbers continue to rise, forcing insurers to reassess their approach to measuring risks, issuing pricing, and enforcing controls upon their clients to help mitigate the potential of a cyber incident.
Data Breach Laws & Regulations
While many states currently have their own privacy and data breach notification laws in place, lawmakers are advancing the ball to bring federal requirements to the table due to the increasing number of cyber-related attacks across all sectors. Case law related to data breaches is constantly emerging and teaches us about the minefield of legal exposure in this area, which is why specialized counsel is crucial in the event of a cyber incident (often referred to as a data breach coach). The CapitalOne issue is a great example of how attorney-client privilege can be easily lost due to how incident responders are contractually engaged, as well as the oversharing of confidential findings within an organization.
The New York Department of Financial Services (NYDFS) is actively enforcing their cybersecurity regulations by issuing steep fines to financial institutions that fail to comply with their prescribed requirements. While business email compromises are sadly an everyday occurrence, they can be mitigated with proper implementation and management of security controls. Yet somehow, these types of cyber incidents continue to happen, which is why state and federal agencies are becoming more stringent in their response to these incidents.
An example of this is a mortgage company that failed to disclose a business email compromise, which resulted in a $1.5 million penalty. Another case identified a life insurance company’s failure to implement multi-factor authentication, which ultimately led to successful malicious email phishing attacks compromising several email mailboxes containing sensitive information; the insurance company was fined $1.8 million for their non-compliance and the consequential outcome.
More recently, the Securities and Exchange Commission fined multiple firms due to lax cybersecurity policies and controls, which resulted in numerous email account takeovers exposing thousands of consumers personally identifiable information (PII) records. And then, there’s the first ever sanction of its kind by the U.S. Department of the Treasury where a cryptocurrency exchange (Suex) was fined for facilitating illicit payments in conjunction with at least eight ransomware variants.
These actions by the federal government are indicative of the continued fight against ransomware and other cyber-related attacks. It’s easy to see that these fines will continue to mount until organizations of all sizes take security seriously. Some states have introduced safe harbor legislation to promote the adoption of industry-recognized cybersecurity frameworks to help protect a compliant business from certain legal claims within said state in the event of a cyberattack. If followed (as outlined by the specific state law), these breach litigation safe harbors can create an affirmative defense when dealing with the legal aftermath of an attack. 2022 will be an interesting year as we continue to watch things unfold as it relates to cyber and privacy law.
Advancements in Proactive Research and Knowledge Sharing
The financial industry is strategically fighting back by investing in open-source intelligence which provides insight into an organization’s footprint on the web. Georgia State University’s Evidence Based Cybersecurity Research (EBCS) Group goes a step further to truly understand how online criminals operate and how organizations can get ahead of future threats based on identified trends. The Federal Reserve Bank of Atlanta recently partnered with EBCS to monitor online criminal markets for payments-related activity to document trends, identify new types of fraud, and support a better understanding of crimes surrounding new payment types. Through this partnership, the FRB of Atlanta is taking proactive measures in the prevention of cyberthreats and online payment fraud.
Professionals in the financial sector have most likely heard of or are a member of The Financial Services Information Sharing and Analysis Center (FS-ISAC), which is the only global cyber intelligence sharing community solely focused on financial services. Members receive a myriad of benefits surrounding sector-specific cybersecurity insights, guidance, alerts, tools, and access to a network of experts to prepare for and mitigate cyberthreats.
Planning Ahead to Aid in the Prevention of Cyberattacks
Most (not all) cyber-related incidents can be avoided through proper planning and by having the right resources in place. Preparation is what makes all the difference, which entails outlining your risks, implementing safeguards to aid in prevention, and knowing who to bring in and when in the event of a cyber incident. After a cyber incident has occurred, time is of the essence to lessen the overall damage.
While defense-in-depth is key to any well-rounded cybersecurity program, it all starts with having the right approach in place focused on people, process, and technology – in that order. Some companies get ahead of themselves and throw money at technology without having the right people and processes in place to manage it. This method never works, as technology alone cannot get the job done.
People – There are multiple ways to touch on the “people” aspect of this approach, many of which vary on the industry and size of the organization. Organizations at the very least should have the right people in place (and enough of them) to perform the work necessary, whether internally or outsourced.
- Executives and board members are expected to make cybersecurity a priority and discuss it on a regular basis to ensure the business has the information and resources it needs to address cyber threats.
- The business should have cyber liability coverage in place with oversight by an executive or manager who understands the policy requirements and limits, and how/when to invoke the policy.
- Risk management personnel know how to measure risk appropriately to ensure that business operations and financial success align with the Organization’s risk appetite.
- IT teams should be knowledgeable about how to implement and maintain proper IT and security controls.
- Cybersecurity professionals should help build out security programs and applications, assess the controls in place through security audits, and investigate threats.
- Employees should receive regular and meaningful security awareness training, so they are prepared for the threats they may encounter and how to report and respond to them.
- Outside counsel specialized in privacy and cybersecurity (a.k.a. data breach coaches) and digital forensics and incident response firms should be vetted and ready to respond, when needed. Some cyber insurance carriers utilize a panel of approved legal and incident response providers they bring in at the onset of a claim, whereas others allow the business to form relationships and select the vendors of their choosing.
Process – Once you know who the people are and the parts they play, you need to define the why, how, and when they do it.
- Some industries are required to follow certain types of regulatory compliance frameworks (i.e., HIPAA, FISMA, etc.), while others may undergo an elective security audit and certification process (i.e., SOC2, ISO27001, etc.) due to client requirements. Whatever the case may be, the organization should know the compliance framework(s) they are subject to or intend to follow and implement policies and procedures to ensure strict adherence by all involved.
- Organizations need metrics to measure success. Define expectations and processes and audit them regularly to identify strengths and weaknesses. This includes testing your incident response plan at least annually.
- The IT team should define a cadence for applying security patches based on the criticality and risk of exploitation. This ensures the riskiest vulnerabilities are addressed first during patching.
- Define how often assessments are done, such as risk assessments, penetration testing, cloud control reviews, and so on. Having scheduled assessments in place aids in repetition to ensure continuous evaluation and remediation of risks.
- Cybercriminals can strike anytime, but we are now beginning to see a trend that attacks occur during the holidays and weekend, as outlined by CISA in a recent statement. Having the right processes (and people) in place can help mitigate the risks during these times.
Technology – People define processes and use technology to meet their needs. People should vet and compare technological solutions to align with expectations.
- Identify and implement (in no particular order):
- Antivirus and endpoint detection and response solutions
- Vulnerability scanners (network + agent-based) and patching deployment software
- Asset management technologies
- Multi-factor authentication
- SIEM
- Network segmentation
- Data backup solutions
- Remote access software/VPN
- Device controls
- Password vaulting solutions
- Encryption (at rest and in transit)
- Sensitive data scanning solutions
- Geographical controls
- DMARC, SPF, and DKIM
- Honeypots/canary tokens
The above is a non-exhaustive Iist but should give readers an idea of things to consider when layering in the components of a good cybersecurity program. If you need assistance, Avalon Cyber provides several services that can help your organization prepare for and respond to cyber threats, including penetration testing, vulnerability assessments, managed detection and response, managed SIEM, and incident response.
There’s no doubt that the financial sector is a high-value target, which is why organizations in this industry must be diligent in their efforts to protect their data and systems. Security is no longer a choice; it is a business expense and a necessity to operate in this digital age where everything and everyone is connected online.
If you would like to discuss any of our services, contact one of our experts today.
Brandy Griffin is the Director of Cybersecurity Operations, where she manages a team of cybersecurity professionals and works alongside the sales and leadership teams to meet the company’s goals. She continues to support our clients' needs on a daily basis and ensures we always deliver high-quality services. Brandy’s experience in cybersecurity is further complimented by her skills in eDiscovery and digital forensics from previous positions she’s held at Avalon and her past employer, a fortune 1000 Company.