As a teenager back in the ‘90s, some of my favorite things to do included playing PlayStation and eating pizza. If I were a teenager today, the only difference would be that I’d be playing on my laptop or tablet while eating pizza. Alas, today, I am an adult. And instead of playing games, I’m going to conferences.
In mid-August I attended the annual International Legal Technology Association conference (ILTACON) in the D.C. area and, as usual, I caught a number of interesting educational sessions. One of the very best, in my opinion, was titled “Watch a 15 Year Old Hack Your Firm’s Users.” How could I not go to see that, right?
Sure enough, there was 15-year-old running the session—which was standing room only—with the help of his father. He showed us all sorts of cheap tools he bought on eBay or Alibaba for less than $10. Additionally, he demonstrated some of the strategies he uses—fake public WiFi networks, social engineering, keyloggers, and unsecure WordPress sites. He combines these tools and strategies to hack networks, gather peoples’ usernames and passwords, and hacks in to see what he could find about these unsuspecting people. The same people that probably work for your company.
The questions you would expect to hear inevitably came up:
How did you learn to do this?
He learned this from trial and error and searching Google, of course. He admitted to having killed a couple laptops along the way but, all in all, he had spent no more than a regular teenager’s allowance to buy gadgets online and teach himself how to hack.
What are you doing with the information you find?
For now, he says he doesn’t do anything with the information he gathers. It’s just another video game to him—can I get in? What can I find? That’s about it.
But if you’re anything like me, you’ll agree that, for every well-intentioned 15-year-old, there are about 100 that don’t handle temptation and mischief quite as maturely.
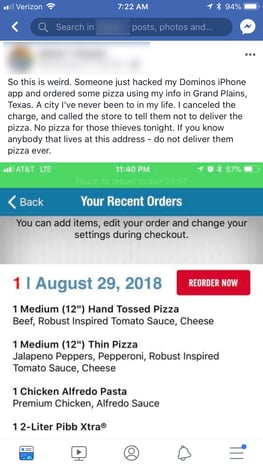
A couple of weeks after the conference, I was scrolling through Facebook and saw that a friend of mine posted that his Domino’s pizza app was hacked. Someone had ordered two pizzas, chicken alfredo, and Mr. Pibb to an address in a town in Texas that he’s never even been to. I can’t pretend that I didn’t think it was funny…especially the chicken alfredo order (and how do you not at least add some cheesy bread to that order?).
After my amusement subsided, I began to think who would hack into a Domino’s account?
Then I thought of teenage me. He’d probably be interested in trying to get a free pizza. So I’m banking on this particular hack being the work of a teenager just getting into some mischief.
But today’s reality is that there is no common demographic for a hacker—they come in all shapes, sizes, ages, genders, and ethnicities, and have a range of motivations, from stealing information to sell on the dark web to ordering some chicken alfredo to help fuel an all-night binge with friends. Also, there’s no special training needed and no significant financial investment to get started.
So how do you protect yourself and your company against risks that are constantly evolving with all sorts of data they are after? It’s not easy. It requires a constantly evolving strategy that is moving just as fast as the threat landscape. It requires a team, technology, and partners that work harder than those that are trying to score some free pizza and the company’s crown jewels.



